1. Article purpose[edit | edit source]
This article explains how the Arm® TrustZone® execution context is used for on an STM32 MPU-based platform.
2. Introduction[edit | edit source]
The STM32 MPU is based on the Arm® Cortex®-A core, which is using the Arm® TrustZone[1] architecture that enables context isolation: the normal world holds the applications whereas the secure world isolates all the trusted applications and core secure services so that they can safely manipulate platform secret data. The MPU includes firewall mechanisms that allow the secure world to forbid read/write accesses from the normal world to given peripherals.
3. ARMv7-A[edit | edit source]
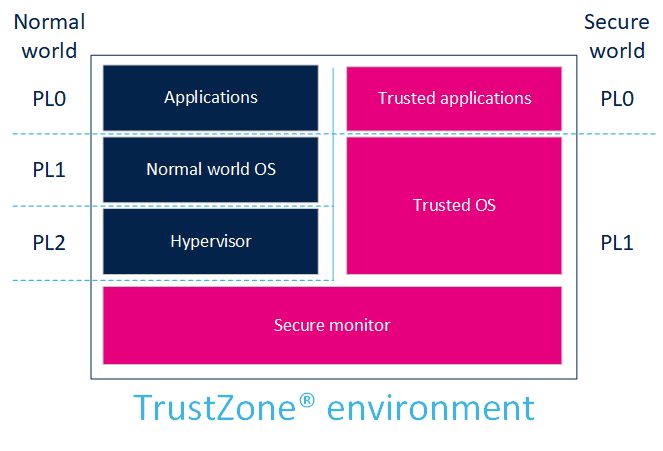
ARMv7-A defines PL0, PL1 and PL2 privilege levels:
- PL0 is the lowest software privilege level (unprivileged calls allowed for applications).
- PL1 is the privilege level for the OS.
- PL1 (secure) is also the privilege level for secure monitor execution, to switch from the secure to the normal world.
- PL2 is dedicated to the hypervisor (only non-secure).
4. ARMv8-A[edit | edit source]
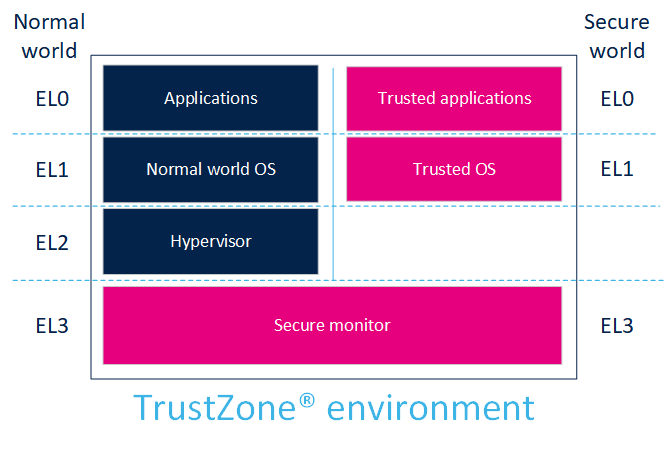
ARMv8-A defines EL0, EL1, EL2, EL3 execution levels:
- EL0 is the lowest software execution level (unprivileged calls allowed for applications).
- EL1 is the execution level for the OS.
- EL1 (secure) is also the privilege level for secure monitor execution, to switch from the secure to the normal world.
- EL2 is dedicated to the hypervisor (only non-secure).
- EL3 is the highest execution level where the switch between non-secure and secure is possible.
5. Software integration[edit | edit source]
The normal world is used to run rich OSs such as the Linux® kernel and its applications framework.
The secure world runs a TEE as the secure OS (for example OP-TEE OS).
In 32-bit mode (ARMv7-A), the secure monitor is included in the secure OS.
In 64-bit mode (ARMv8-A), the secure monitor is a dedicated software Trusted Firmware-A (BL31).
The TrustZone environment is a complete system solution that is not limited to the Cortex® context. It provides a bus and peripheral infrastructure to the MPU to ensure that the secure world relies on a completely secured pipe when it controls a secure peripheral. The assignment of the peripherals to a given world is done through a firewall mechanism, which is set up during the secure world initialization.
Dedicated secure and normal contexts also impact the debugging facilities: depending on the targeted user, the debug can be opened to both worlds (for instance for a secure-aware developer), to the normal world only (for a Linux® developer), or completely closed (for the end user). This is achieved by configuring the debug control.
Some internal or external peripherals can be used by the secure world to support cryptographic operations.
6. References[edit | edit source]