Template:ArticleMainWriter Template:ArticleApprovedVersion
1. Purpose[edit | edit source]
Secure boot is a key feature to guarantee a secure platform.
STM32MP1 boot sequence supports a trusted boot chain that ensures that the loaded images are authenticated and checked in integrity before being used.
2. Authentication processing[edit | edit source]
2.1. STM32 Header[edit | edit source]
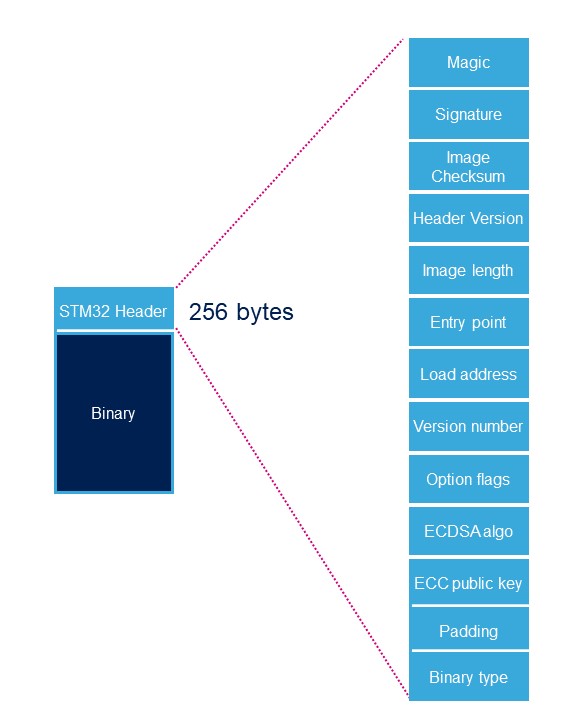
Each signed binary image includes a specific STM32 header added on top of the binary data. The header includes the authentication information.
| Name | Length | Byte Offset | Description |
|---|---|---|---|
| Magic number | 32 bits | 0 | ‘S’ ; ‘T’ ; ‘M’ ; 0x32 |
| Image Signature | 512 bits | 4 | ECDSA signature for image authentication1 |
| Image Checksum | 32 bits | 68 | Checksum of the payload2 |
| Header version | 32 bits | 72 | Header version v1.0 = 0x00010000 Byte0: reserved Byte1:major version = 0x01 Byte2: minor version = 0x00 Byte3: reserved |
| Image Length | 32 bits | 76 | Length of image in bytes3 |
| Image Entry Point | 32 bits | 80 | Entry point of image |
| Reserved1 | 32 bits | 84 | Reserved |
| Load address | 32 bits | 88 | Load address of image4 |
| Reserved2 | 32 bits | 92 | Reserved |
| Version Number | 32 bits | 96 | Image Version (monotonic number)5 |
| Option flags | 32 bits | 100 | b0=1: no signature verification6 |
| ECDSA Algorithm | 32 bits | 104 | 1: P-256 NIST ; 2: brainpool 256 |
| ECDSA Public key | 512 bits | 108 | ECDSA public key to be used to verify the signature.7 |
| PAD | 84 Bytes | 172 | Reserved padding bytes8. Must all be set to 0 |
- 1 Signature is calculated from first byte of header version field to last byte of image given by image length field.
- 2 32-bit sum of all payload bytes accessed as 8-bit unsigned numbers, discarding any overflow bits. Used to check the downloaded image integrity when signature is not used (if b0=1 in Option flags).
- 3 Length is the length of the built image, it does not include the length of the STM32 header.
- 4 This field is used by ROM code for specific executable images.
- 5 Image version is an anti rollback monotonic counter. The ROM code checks that it is higher or equal to the monotonic counter stored in OTP.
- 6 Enabling signature verification is mandatory on secure closed chips.
- 7 Hash of (algorithm+pubKey) is stored in OTP WORD 24 to 31.
- 8 This padding forces Header size to 0x100 bytes.
2.2. Verification[edit | edit source]
STM32 MPU provides authentication processing with ECDSA [1] verification algorithm, based on ECC [2]. ECDSA offers better result than RSA with a smaller key. STM32 MPU relies on a 256 bits ECDSA key.
Two algorithms are supported for ECDSA calculation:
- P-256 NIST
- Brainpool 256
The EDCSA verification follows the process below:
The ROM code provides secure services to the FSBL for image authentication with the same ECC pair of keys, so there is no need to support ECDSA algorithm in FSBL.
OTP WORD 24 to 31 are used to store the public key hash (PKH).
3. Secure boot feature enabling[edit | edit source]
3.1. Host processing tools[edit | edit source]
First step is to generate the ECC pair of keys with STM32 KeyGen tool. This is the key pair that will be used to sign the images.
The tool also generates a third file containing the public key hash (PKH) that will be used to authenticate the public key on the target.
In a second step, FSBL and SSBL binaries must be signed. STM32 Signing tool allows to fill the STM32 binary header that is parsed by the embedded software to authenticate each binary.
Once those steps are done, the images are ready to be programmed into the flash on the target board with STM32CubeProgrammer.
3.2. Target configuration[edit | edit source]
3.2.1. Register hash public key[edit | edit source]
First step to enable the authentication is to burn the OTP WORD 24 to 31 in BSEC with the corresponding public key hash (PKH, output file from STM32 KeyGen).
OpenSTLinux embeds a stm32key tool that can be called from U-Boot command line interface to program the PKH into the OTP.
PKH file (publicKeyhash.bin) must be available in a filesystem partition (like bootfs) on a storage device (like sdcard) before proceeding.
ext4load mmc 0:4 0xc0000000 publicKeyhash.bin Load hash file from mmc 0 partition 4 (ext4) in DDR
32 bytes read in 50 ms (0 Bytes/s)
stm32key read 0xc0000000 Read loaded key from DDR to confirm it is valid (without writing it in OTP) OTP value 24: 12345678 OTP value 25: 12345678 OTP value 26: 12345678 OTP value 27: 12345678 OTP value 28: 12345678 OTP value 29: 12345678 OTP value 30: 12345678 OTP value 31: 12345678
stm32key fuse -y 0xc0000000 Write key in OTP
The device now contains the hash to authenticate images. The images and boot can now be flashed.
Without any other modification, the device is able to perform image authentication but non authenticated images can still be used and executed: the device is still opened, let's see this as a kind of test mode to check that the PKH is properly set.
3.2.2. Bootrom authentication[edit | edit source]
Using a signed binary, the ROM code authenticates and starts TF-A.
If authentication fails, the ROM code enters into a serial boot loop indicated by the blinking Error LED (cf Bootrom common debug and error cases)
3.2.3. TF-A authentication[edit | edit source]
TF-A is in charge of loading and verifying U-boot and (if used) OP-TEE image binaries.
Each time a signed binary is used, TF-A will print the following status:
INFO: Check signature on Non-Full-Secured platform
If the image authentication fails the boot stage traps the CPU and no more traces are displayed.
3.2.4. Close the device[edit | edit source]
As soon as the authentication process is confirmed, the device can be closed and the user forced to use signed images.
OTP WORD0 bit 6 is the OTP bit that closes the device. Burning this bit will lock authentication processing and force authentication from Bootrom. Non signed binaries will not be supported anymore on the target.
To program this bit, the STM32CubeProgrammer or U-Boot command line interface can be used. Here is how to proceed with U-Boot:
fuse 0 0x0 0x40