How to start with OEMiRoT on STM32U385 - Arm® TrustZone® enabled![]() 85min
85min
Literature
- RM0487 STM32U3 Reference Manual (not yet officially available)
- UM2237 STM32CubeProgrammer software description
- UM2238 STM32TrustedPackageCreator tool software description
- AN5054 Secure programming using STM32CubeProgrammer
- AN2606 STM32 microcontroller system memory boot mode
- It is advised to read the RDP for STM32U3 article.
- It is advised to read the OEMiRoT_OEMuRoT_for_STM32U3 article.
Target description
The purpose of this article is to explain step by step how to use the OEMiRoT STM32CubeFW example provided by ST.
The provided example is using the STM32U385 Nucleo board, a device embedding hardware cryptographic accelerators (contrarily to STM32U375).
No example is provided for the STM32U375 and no ST board is available for this device.
But OEMiRoT is possible for the STM32U375 using mbed-crypto middleware.
Introduction
Through this practical example, the user will learn how to perform the following operations
- Run the OEMiRoT example of the STM32CubeFW
- Provisioning preparation
- Code and data compilation and encrypted image generation
- Perform the provisioning and install the firmware and data files
- Execute the installed firmware
- Modify the user application and perform a firmware update
- Perform a full regression
- Provisioning in RDP>0
- Regression using password
Prerequisites
- Hardware
- U385RG-Q Nucleo board (MB1841)
- Required tools
- STM32Cube_FW_U3_V1.1.0 [1] or upper
- STM32CubeProgrammer[2] Software programming tool for STM32 (STM32CubeProgrammer API v2.18.0-RC3 or later version)
- Including STM32TrustedPackageCreator
- IAR Embedded Workbench rev 9.20.1 + patch STM32U37x-38x
- The patch is available in the STM32CubeFW: STM32Cube_FW_U3_Vx.x.x\Utilities\PC_Software
- Tera Term or equivalent UART Terminal emulator
- Environment setup
- Download the STM32CubeU3 package and install it
- A directory NUCLEO-STM32U385RG-Q is included in the CubeFW Projects directory.
- The ROT_Provisioning\OEMiRoT directory contains the different tools, configuration files and scripts.
- The Applications\ROT directory contains the different code examples used in this step by step.
1. OEMiRoT configuration and launch of the provisioning script
This chapter explains how to start with the configuration and launch of the provisioning script.
1.1. Setting of the images configuration
- Open the flash_layout.h using a text editor:
- STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\Applications\ROT\OEMiROT_Boot\Inc
The flash_layout file defines different settings such as the flash area split and the number/type of images.
- For this tutorial, set the data images for secure and non-secure as shown in the figure above and keep the default settings for all other parameters.
- The image generation for the user application and data will be explained later in this article.
1.2. Launch the provisioning script
The scripts are located in \Projects\NUCLEO-U385RG-Q\ROT_Provisioning\OEMiROT.
- Launch one of the provided scripts depending on your IDE:
- For EWARM or MDK-ARM: launch the provisioning.bat script.
- For STM32CubeIDE: launch the provisioning.sh script.
- Keep the script running during the complete process, it will guide you through all the steps.
1.2.1. RDP level selection
- As indicated by the script, the RDP level needs to be defined.
- it is advised to make first trials in RDP0.
- Before increasing the RDP level, ensure to have a good understanding of the role of the other RDP levels.
- Refer to the RM0487 and to the documentations indicated at the beginning of this article.
1.2.2. Authentication and encryption keys setting
- Open TrustedPackageCreator (TPC)
- Select the "Shield" Icon and open the OEMiRoT_Config.xml file, as show in the figure below.
- Three different keys are shown.
- The authentication key for the Secure application/data and the Non-Secure application/data.
- The key for the encryption of the applications and data.
- The default keys are advised to be used for trials.
- For a commercial product, obviously the keys need to be regenerated.
- The keys can be regenerated using TPC.
- Keep the path and name for the output file as shown in the figure. This file will be used by the script during the provisioning.
- Click on "Generate OBkey" (right bottom of the TPC window, not shown in the figure above)
- The OEMiRoT_Keys.bin file is generated in the ROT_Provisioning\OEMiROT\Binary folder.
2. Code and data images generation
2.1. OEMiRoT_Boot firmware compilation
A boot firmware example is provided in the CubeFW for the different supported IDE.
For this tutorial IAR Embedded Workbench is used.
- Open the OEMiRoT_Boot project with your preferred tool chain.
- The OEMiRoT_Boot firmware is available at: STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\Applications\ROT\OEMiROT_Boot
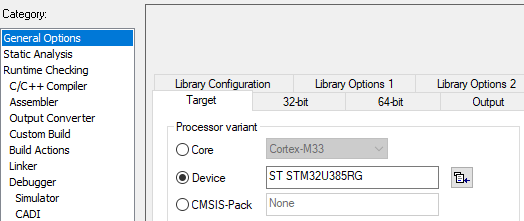
- STM32U385RG should be automatically selected in the product option (see figure below)
- For IAR: menu: Project -> Option -> General Option
- If it's not the case, please check if your IDE version is supporting this product or if the STM32U3 patch is correctly installed (see prerequisites at the beginning of this article)
- Perform: Project -> Rebuild All (don’t upload the code, only perform a compilation)
2.2. User application code compilation
As indicated by the script, the next step is to compile the user application.
The user application is split into two parts: a secure application and a non-secure application.
- Open the OEMiRoT_Appli_TrustZone application code using your preferred tool chain.
- STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\Applications\ROT\OEMiROT_Appli_TrustZone\EWARM
- Verify that the STM32U385 appears in the menu: Project -> Option -> General Option (see figure 6)
- Open Project -> Option -> Build Actions and check the correct paths for the command line (see figure below)
- Through the postbuild command, the binaries are automatically encrypted and signed using the keys defined in the section "Authentication and encryption keys setting".
- As shown in the figure below, the user application code example is divided in two different codes, one secure and one non-secure.
- Compile first the secure code: click right on "Appli_TrustZone_S" => RebuildAll (don’t upload the code, only perform a compilation)
- Proceed in the same way to compile the "Appli_TrustZone_NS".
- As shown in the figure below for each user application a binary is created and through the postbuild command encrypted and signed binaries are also created.
- Notes
- The encrypted and signed images generation for the secure and non-secure application codes can also been done graphically using STM32TrustedPackageCreator (TPC). How to proceed is shown in the next section for the data images creation.
- The OEMiROT_S_Code_Image.xml and the OEMiROT_NS_Code_Image.xml files can be open with TPC.
- These files are located in the same folder as for the data (see next section).
- The dependencies with other images can also be managed.
- These .xml files can also be directly edited with a text editor and changes done directly (e.g. image dependency).
- In case of modifications of these xml files relaunch the IDE compilation and the new encrypted and signed images will be created though the postbuild command.
- The encrypted and signed images generation for the secure and non-secure application codes can also been done graphically using STM32TrustedPackageCreator (TPC). How to proceed is shown in the next section for the data images creation.
2.3. Secure data image generation
As indicated by the script the next step is to generate the encrypted and signed images of the data.
- A binary file for the secure data and a binary file for the non-secure data are provided as exemple.
- s_data.bin and ns_data.bin in folder Projects\NUCLEO-U385RG-Q\ROT_Provisioning\OEMiROT\Binary
- These files can be open using STM32CubeProgrammer => tab "Open file" => select s_data.bin or ns_data.bin.
- To generate the encrypted and signed images of these data files launch STM32TrustedPackageCreator.exe
- Click on shield and open the OEMiROT_S_Data_Image.xml file located in the OEMiRoT/Images folder (see figure below)
- Click on "Generate Image"
2.4. Non-Secure data image generation
- Proceed in the same way as explained in the previous section to generate the non-secure data image
- Open the OEMiROT_NS_Data_Image.xml file and generate the image
- As shown in the figure below two new files have been created: s_data_enc_sign.bin and ns_data_enc_sign.bin
3. Board Provisioning
- Connect the Nucleo board using the USB STLK port.
- The script will automatically perform the provisioning of the device using all the files generated during the previous steps.
3.1. Boot pin to set to VSS
- As indicated by the script, the boot pin needs to be set to VSS (through the on board-pull down on the pin5 of CN7).
3.2. OTP programming and flash programming
As indicated by the script the OEM2 key is provisioned.
For RDP0 level the provisioning of this key would not be needed, but the script will perform it by default.
The advantage is that the regression of the board will always be possible, also in case accidentally the user sets the device to RDP2.
- An example password file is provided: \Projects\NUCLEO-U385RG-Q\ROT_Provisioning\OEMiROT\Keys\oem2_password.txt
- For trials it's advised to use this default value text file.
- For commercial products obviously, a personal password has to be defined and kept secret in order to be able to make a regression if needed in future.
- The script will automatically set the OTPs and install the different codes and data.
- As shown in the figure below, at the end of the automatic process, a message is displayed confirming that the board is correctly provisioned.
- Close the script
4. Execution of the installed application
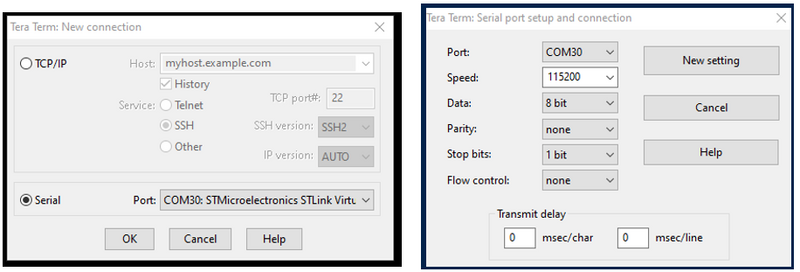
- Open Tera Term (or another terminal emulator)
- Select “ Serial” and the COMxx port related to the STLink
- Setup -> Serial port …
- Set speed to 115200 and data to 8 bit
- Click: New Setting
- Reset the board (black reset button)
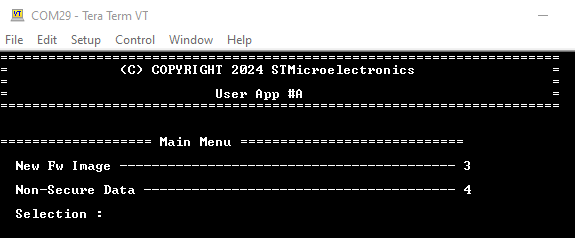
- The code installed during the previous steps is executed
- The different menus can be tried out typing the related number on your keyboard.
5. Regression
A regression will re-intialize the device, removing all the installed applications and option byte settings.
- If connected to the device, close the Tera Term or STM32CubeProgrammer.
- Launch the regression.bat or regression.sh script located in: STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\ROT_Provisioning\OEMiROT
- When the regression is completed a confirmation message is displayed according to the figure below.
- With STM32CubeProgrammer the flash and option bytes can be readout to verify that the device has been reinitialized.
6. RDP1 provisioning
The provisioning in RDP1 is not described in this article.
- After a regression the provisioning script can be launched again and the RDP1 can be defined.
- The best way to proceed is to follow all the indications of the provisioning script and to regenerate all the firmware images.
- Reminder: in RDP1 using STM32CubeProgrammer, it is not possible to read the content of the flash since readout protected, but it is possible to read the Option Bytes values.
7. RDP2 provisioning and Firmware Update
7.1. Provisioning in RDP2
Previous sections are describing how to use the script, generate the different encrypted and signed images and perform the board provisioning.
- Disconnect and reconnect the USB cable to perform a power on reset.
- Launch the provisioning script (STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\ROT_Provisioning\OEMiROT\provisioning.bat or .sh).
- For EWARM or MDK-ARM: launch the provisioning.bat script.
- For STM32CubeIDE: launch the provisioning.sh script.
- All the steps requested by the script are described in the previous sections.
- The last provisioning steps are shown in the figure below.
- The RDP has been set to level 2.
- A confirmation of correct programming is indicated as shown in the figure.
- Launch STM32CubeProgrammer and try to connect the board.
- Since the device has been set to RDP2 the debugger is disabled.
7.2. Execute installed application in RDP2
As explained in previous section, execute the installed application as following:
- Open Tera Term (or another terminal emulator)
- Select “ Serial” and the COMxx port related to the STLink
- Setup -> Serial port …
- Set speed to 115200 and data to 8 bits
- Click: New Setting
- Keep the script open
7.3. User application update
7.3.1. User application modification
- Open the user application with your preferred tool chain: STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\Applications\ROT\OEMiROT_Appli_TrustZone
- Modify the non-secure application, for instance as shown in the figure below
- Compile the code without uploading the application (don't connect to the board)
- Through the postbuild, a new encrypted and signed binary has been automatically created: STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\Applications\ROT\OEMiROT_Appli_TrustZone\Binary\rot_tz_ns_app_enc_sign.bin
- In the script, type 3 to launch the upgrade menu.
- Type 3 to select the NonSecure user application download.
- The new encrypted and signed binary can be transferred in the dedicated download slot of the device using the YMODEM protocol.
- This can be done directly using your terminal emulator as shown below for Tera Term.
- If applicable, other new generated images can also be uploaded typing the corresponding number and using the previous procedure.
- Perform a reset pushing the black button of the Nucleo board.
- The modified user application is executed (#B).
A new application has been installed without requiring a regression, the device has been kept in RDP2
7.4. Regresssion
- The debugger is deactivated since the device is in RDP2. A connection trial using CubeProgrammer will generate an error.
- Unplug and replug the USB cable of the board to perform a hardware reset.
- Launch the script: STM32Cube_FW_U3_Vx.x.x\Projects\NUCLEO-U385RG-Q\ROT_Provisioning\OEMiROT\regression.bat or .sh
- Note:
- The regression from RDP2 is possible thanks to the previously provisioned OEM key2.
- The technical background is explained in section 3.10.1 of RM0487. Check the impact of the OEM Lock option byte (table 16 of RM)
- The regression script is performing automatically all the needed operations to regress from RDP2 to RDP1 and in a second step from RDP1 to RDP0.
- Proceed as mentioned in the script, unplug and replug the USB cable and click to continue the script execution
- As shown in figure above, the script is unlocking the RDP2 using the provisioned password.
- After a successful execution, the script will end as shown below.
8. Appendix
8.1. STLink firmware update
The Nucleo board embeds an STLink.
It is advised to have the latest STLink firmware installed on the board.
To perform the update, proceed as follows (see picture below):
- The board must be connected with the USB STLink cable.
- Open the STM32CubeProgrammer but don't connect the device
- Click:
- "Firmware upgrade"
- Open in update mode
- Tick "Change Type"
- Tick "STM32Debug + VCP" (for OEmiRoT, it is advised to select the option without the Mass storage)
- "Upgrade"
9. References