{{ArticleBasedOnModel | Example tech domain article}}
1. What is the Cryptographic Library
The Cryptographic Library V4.x.x supports most of required algorithms for encryption, hashing, message authentication and digital signing, enabling developers to meet application requirements for any combination of data, integrity, confidentiality, identification/authentication, and non-repudiation.
The Cryptographic Library is designed and compiled to run on Arm® Cortex®-M based ST MCUs.
| File:Info.png | Note: Arm® is a registered trademark of Arm Limited (or its subsidiaries) in the US and/or elsewhere. |
2. Getting started with STM32 and the Cryptographic Library
Cortex®-M Optimized Crypto Stack (CMOX) is an optimized Cryptographic Library to be used with STM32 Cortex®-M based MCUs.
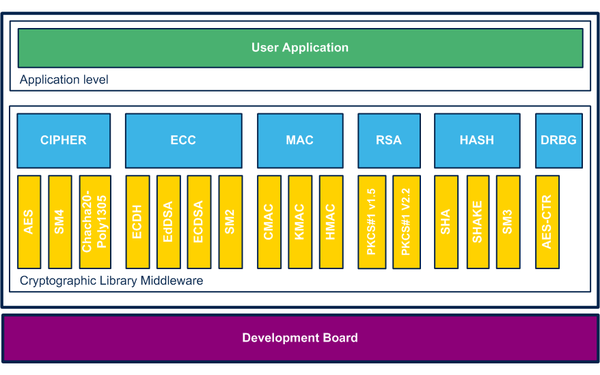
Supported cryptographic algorithms:
- Cipher encryption and decryption:
- AES: CBC, CCM, CFB, CTR, ECB, GCM, OFB, XTS, KeyWrap
- SM4: CBC, CFB, CTR, ECB, OFB
- Chacha-Poly1305
- Digest generation:
- SHA-1
- SHA-2: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256
- SHA-3: SHA3-224, SHA3-256, SHA3-384, SHA3-512
- SM3
- SHAKE
- Message authentication code (MAC) generation:
- HMAC:
- SHA-1
- SHA-2: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256
- SM3
- AES: CMAC
- KMAC: SHAKE
- HMAC:
- Elliptic curves based on key generation, signature and verification:
- Elliptic curve digital signature algorithm (ECDSA): NIST-R (P-224, P-256, P-384, P-521), NIST-K P-256, BRAINPOOL R/T (P-160, P-192, P-224, P-256, P-320, P-384, P-512), ANSSI P-256
- Edwards-curve digital signature algorithm (EdDSA): Ed448, Ed25519
- SM2 digital signature algorithm: OSCCA 256-bits curve
- Elliptic curves Diffie-Hellman:
- Curve448, curve25519
- NIST-R (P-224, P-256, P-384, P-521), NIST-K P-256, BRAINPOOL R/T (P-160, P-192, P-224, P-256, P-320, P-384, P-512), ANSSI P-256
- RSA signature, verification, encryption & decryption:
- PKCS#1 v1.5 and v2.2
- Chinese remainder theorem (CRT) key representation
- Hash method:
- SHA-1
- SHA-2: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256
- Deterministic random bit generator (DRBG):
- CTR-DRBG
3. Cryptographic Library compliancy with STM32 MCUs
The delivered libraries (one per each Cortex®-M core) are structured to be compliant with all the cores used by STM32 MCUs. They can thus be used on any STM32 MCU that embeds the corresponding Cortex®-M core.
4. STMicroelectronics resources
The Cryptographic library package can be downloaded from: STM32 cryptographic firmware library software expansion for STM32Cube
| File:Info.png | Export Control: The Cryptographic library delivered binaries are classified ECCN 5D002, thus requiring you to fill in a form and accept Export control regulations Terms & conditions before being able to download the package from st.com. |
| File:Info.png | Licensing: The Cryptographic library V4.x.x delivered binaries are licensed under ST proprietary terms (see details with the downloadable package). |