1. Introduction
In this article, STM32H7RS refers to the STM32H7Rx/7Sx microcontroller product lines.
This article gives an overview about debug authentication applied to STM32H7RS MCUs.
A detailed description of debug authentication is provided in AN6008
If you want to learn more about debug authentication specific usage for each STM32H7RS device and you want to practice, refer to How to start with DA access on STM32H7RS
List of applicable products:
| Type | Products |
|---|---|
| Microcontroller | STM32H7Rxxx, STM32H7Sxxx |
2. Debug authentication setup overview
Here is an overview of the debug authentication setup:
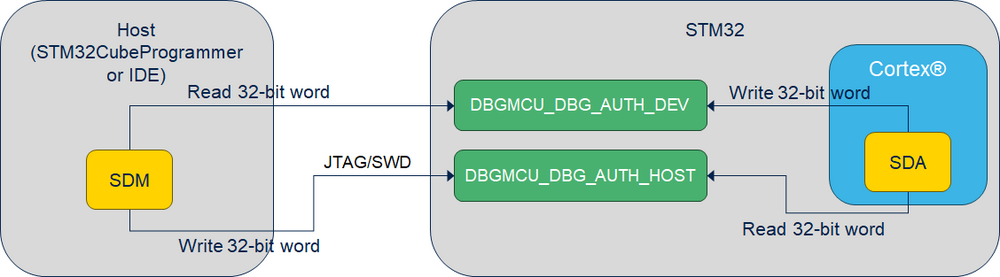
Refer to AN6008 for more details about debug authentication setup.
Refer to Arm® PSA ADAC V1.0[1] for more details about SDM and SDA.
3. Debug authentication services
The debug authentication allows the secure:
- Reopening of the the debug access
- Full regression to product states OPEN
- Download forcing (get access to STMicroelectronics bootloader)
The debug authentication services are usable:
- During development
- For field return analysis
Two authentication methods are available:
- Use of a password. Only a full regression to the OPEN state is possible.
- Use of a certificate chain. Regression and debug opening are possible.
When using certificates, the authorized actions are defined through masks.
Refer to AN6008 for more details about debug authentication certificates, actions, and masks usage.
The debug authentication protocol uses the JTAG dedicated access point (ap0) to communicate with the chip.
The protocol is defined by Arm® in PSA ADAC V1.0[1].
Refer to AN6008 for more details on the debug authentication protocol.
4. Debug authentication provisioning
The debug authentication provisioning consists in storing inside the chip the password hash or the hash of the key related to the root certificate.
These data are stored in OBKey on the STM32H7RS devices.
Refer to AN6008 for more details on the debug authentication provisioning.
5. Reference