1. Article purpose[edit source]
This article explains, step by step, how to run the SSP process from the OEM secret generation till the chip provisioning. The SSP overview is explained here.
This example uses the STM32CubeProgrammer (STM32CubeProg) and its associated tools to manage the complete SSP.
2. OEM secret management[edit source]
The aim of SSP is to protect OEM secrets. It includes multiple secrets:
- Secrets to be provisioned in OTP
- OEM authentication keys for Secure Boot
- OEM secrets encryption key
2.1. Key generation[edit source]
2.1.1. Authentication keys[edit source]
The initial keys to generate for STM32 MPUs are the authentication keys. This is the root of trust of the STM32 MPU secure boot.
The PKHTH (on STM32MP13xC/F lines ![]() ) or PKH (on STM32MP15xC/F lines
) or PKH (on STM32MP15xC/F lines ![]() ) is automatically installed during the SSP process in the dedicated OTP.
) is automatically installed during the SSP process in the dedicated OTP.
To generate the keys, you can use the KeyGen_tool:
Example to generate eight ECC key pairs (Prime256v1) using AES_256_cbc encryption:
STM32MP_KeyGen_CLI -abs /home/user/KeyFolder/ -pwd testkey1 testkey2 testkey3 testkey4 testkey5 testkey6 testkey7 testkey8 -n 8
Example to generate one ECC key pair (Prime256v1) using AES_256_cbc encryption:
STM32MP_KeyGen_CLI -abs /home/user/KeyFolder/ -pwd testkey
2.1.2. Encryption key[edit source]
The SSP process uses a symmetric encryption to protect the OEM secrets exchanged with the chip. This encryption/decryption uses an AES encryption scheme using:
- a 128-bit symmetric key
- a 128-bit nonce value
Both values are first stored in the HSM, and then sent to the chip using a unique chip encrypted flow.
The two values can be directly generated with the STM32 Trusted Package Creator available in STM32CubeProgrammer , which also further manages the secret file encryption with the given key:
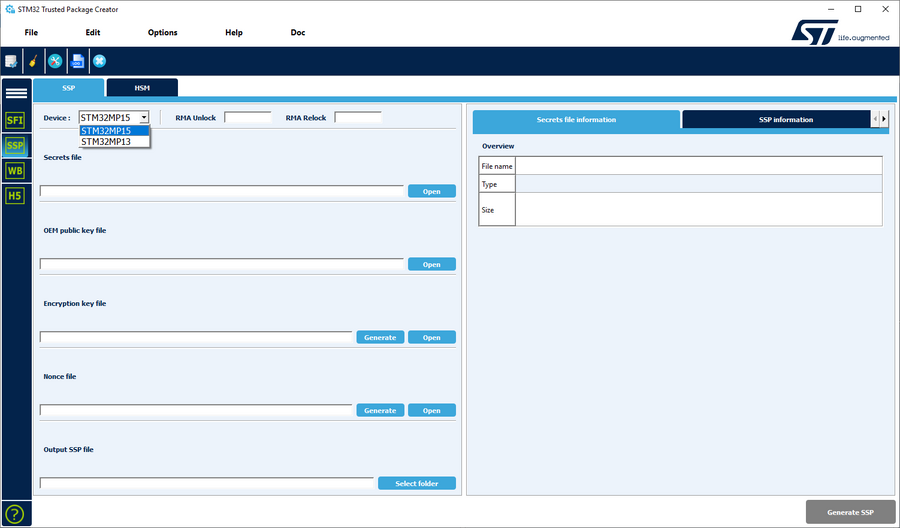
Another solution is to prepare both keys using the KeyGen_tool (till version 2.12.0) with the command:
STM32MP_KeyGen_CLI -rand 16 enc_key.bin
STM32MP_KeyGen_CLI -rand 16 nonce.bin
2.2. Secret file[edit source]
2.2.1. Secret file creation[edit source]
The secret file, which must be generated by the OEM, must represent the OTP 59 to 95 on STM32MP1 Series, named Free for user.
On STM32MP1 Series:
- the words 57 and 58 are reserved for mac_address.
- the final file size must be (96 - 59) * 4 bytes = 148 bytes.
2.2.2. Secret file encryption[edit source]
The STM32 Trusted Package Creator is used to encrypt and prepare the final secret file used for provisioning.
This encrypted final file contains:
- the PKH or PKHTH
- the RMA [1] password
- the OEM secrets
All the previous generated keys must be properly selected in the STM32 Trusted Package Creator interface to generate the final encrypted file (.ssp). The chip and RMA password(s) must be registered in the interface.

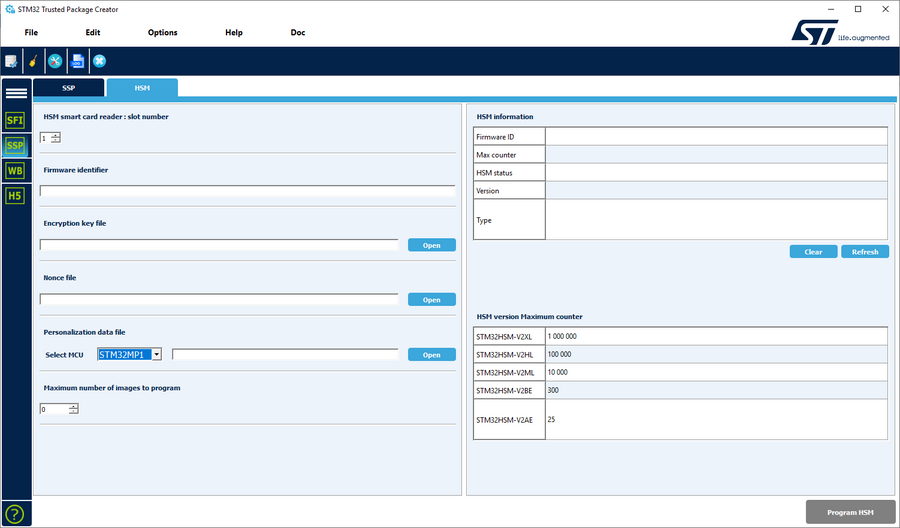
2.3. HSM provisioning[edit source]
The HSMv2[2] must be provisioned with the OEM associated SSP file.
The STM32 Trusted Package Creator has a dedicated SSP HSM provisioning interface to select:
- the encryption key used to encrypt the SSP secret file
- the nonce used to encrypt the SSP secret file
- the personalization data file (used to identify the chip):
- the maximum number of images to program, which depends also on the HSMv2 used
3. SSP Firmware management[edit source]
On STM32MP1 Series, a specific firmware is used to:
- exchange SSP communication with the host,
- burn the OTP in fuses.
This part is managed using a specific TF-A BL2 that is delivered with each ecosystem version and must be updated regarding the user's board.
It only includes a limited part of the TF-A BL2 scope:
- only serial boot support
- dedicated SSP feature set
3.1. TF-A customization[edit source]
The main TF-A firmware is ready for all targets except the board device tree. It must be customized in the same way as for TF-A BL2.
3.2. Build TF-A BL2 SSP[edit source]
Because it uses the same firmware, the way of building and configuring the firmware is described in the How_to_configure_TF-A_BL2 page.
The specific part is the following one:
- dedicated flag to enable the SSP part: STM32MP_SSP
- no TRUSTED_BOARD_BOOT enabled to limit the BL2 binary size
Example:
make ARM_ARCH_MAJOR=7 ARCH=aarch32 PLAT=stm32mp1 STM32MP_UART_PROGRAMMER=1 \ STM32MP13=1 STM32MP_SSP=1 DTB_FILE_NAME=stm32mp135f-dk.dtb
make ARM_ARCH_MAJOR=7 ARCH=aarch32 PLAT=stm32mp1 STM32MP_USB_PROGRAMMER=1 \ STM32MP15=1 STM32MP_SSP=1 DTB_FILE_NAME=stm32mp157c-ev1.dtb
3.3. Signing TF-A BL2 SSP[edit source]
This TF-A BL2 SSP firmware MUST be signed with the OEM authentication key generated at step 1. The authentication is made by the ROM code using the OEM public key given by the HSM during the process.
This is made in the same way as TF-A BL2 using the Signing_tool:
Example :
STM32MP_SigningTool_CLI -bin tfa-ssp.stm32 -pubk OEMpublicKey.pem –prvk OEMprivateKey.pem –pwd testkey
4. Production processing[edit source]
At that stage, the following parts are available:
- SSP encrypted secret file
- provisioned HSM
- TF-A BL2 SSP signed firmware
All that material must be given to the untrusted production to start the SSP process.
4.1. Test case using STM32CubeProgrammer_Cli[edit source]
For an evaluation purpose, STM32CubeProgrammer can be used to test the SSP processing chain.
On the host, the STM32CubeProgrammer must be installed. HSM is plugged into the host smartcard reader. The board is connected, its chip is virgin. The serial boot mode is selected and the power is ON.
The following command can be used for a USB SSP provisioning:
STM32_Programmer_CLI -c port=usb1 -ssp <ssp_file_path> <tf-a-bl2-ssp-path> hsm=1 slot=1
5. SSP : Final state[edit source]
At that stage, the device is provisioned with all the OEM secrets:
- OEM PKH or PKHTH
- OTP secrets
The chip is now in the secure close state; The secure boot is mandatory.
Enabling secure boot is the final step to use the chip.
The SSP process cannot be restarted anymore.
6. References[edit source]