- Last edited one month ago ago
SFI
1 What is SFI?
The secure firmware installation (SFI) solution provides protection when devices are programmed for the first time.
There are two main issues that SFI addresses:
- OEM firmware protection at contract manufacturer (CM) when devices are programmed for the first time
- avoid over production of OEM devices
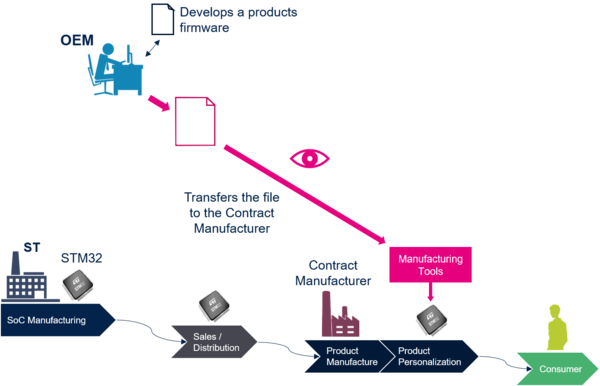
The graph below shows a typical manufacturing process where an OEM develops a firmware and requires this firmware to be flashed to the STM32 during manufacturing. The manufacturing process is the responsibility of the contract manufacturer, that purchases STM32 primary parts from ST through either sales or distribution channels.
In this typical scenario, the OEM sends the firmware to the CM in clear: the application code is potentially exposed to attacks or copy. The OEM must trust the CM, hoping that its application code is not stolen or tampered and that the CM does not over-produce parts.
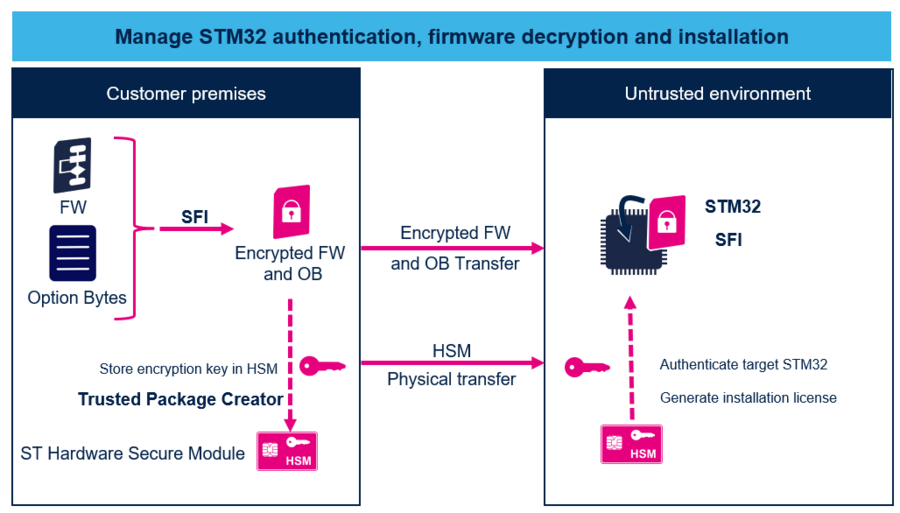
This solution offers a complete example with the STM32 Trusted Package Creator software package to encrypt OEM binaries, the STM32CubeProgrammer to securely flash the STM32, and the STM32-HSM[1] to transfer OEM credentials to the programming partner. The STM32-HSM is an server example. It is possible to create a specific server, without using the HSM.
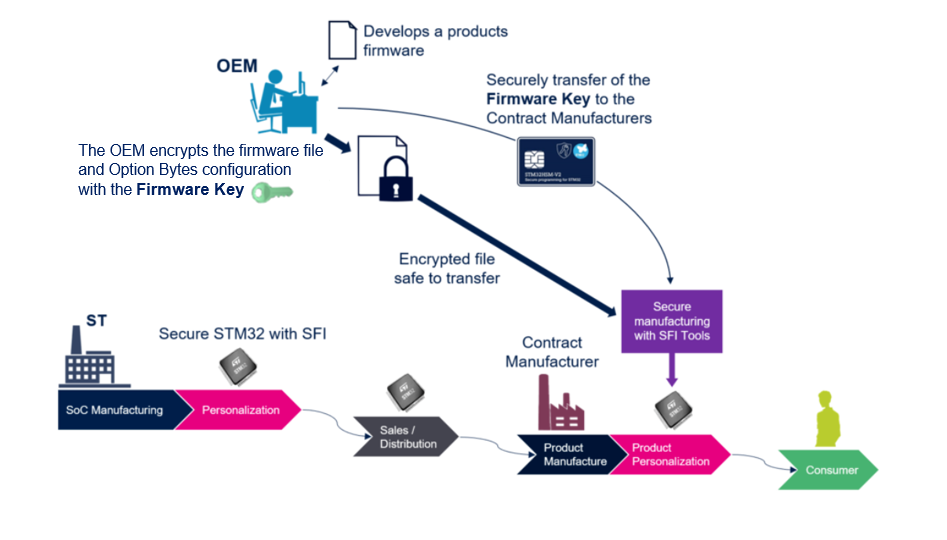
In an SFI-enabled manufacturing, the OEM creates and manages his own secret encryption key, (or firmware key as indicated in the figure below) that is used to encrypt its application code and Option bytes configuration. Then the key is used by the CM for decryption of the SFI package. ST produces secure RSS-enabled STM32, provisioned with a unique private key and certificate, that is available for purchase by the CM through regular sales/distribution channels. The CM is then able to securely install the OEM application code using secure manufacturing SFI tools, so that OEM firmware is never visible in clear at CM level.
The STM32 Trusted Package Creator software is used by OEM to securely encrypt binary files and to store their credentials into STM32-HSM [1]. The STM32CubeProgrammer (or any other SFI recommended partner programming tools) can then be used by the CM to securely program STM32 MCUs in untrusted environments.
2 SFI security features
The SFI security features are the following:
• Only genuine STMicroelectronics STM32 microcontrollers can install the protected
firmware.
• The number of images to program are counted by the STM32-HSM[1].
• Authenticity, integrity and confidentiality of the OEM internal firmware and option bytes are checked and user flash memory is programmed with decrypted firmware and option bytes. If applicable, for the confidentiality of the OEM external firmware, the STM32 receives encrypted OEM external firmware, decrypts this firmware, and re-encrypts with a device unique or global key before programming in external flash memory.
3 Getting started with STM32 and SFI
You can refer to the following pages for step-by-step examples of SFI.
- SFI on Discovery kit STM32H735
- SFIx on Discovery kit STM32H735
- SFI on B-U585I-IOT02A (Under Construction)
4 References